Let’s suppose I decide to run an IPv6-only public hotspot: how many users would be able to surf the web with no troubles? That is, how many devices nowadays run OSs which are able to work out of the box without an IPv4 address?
HTTPS + CT SCT TLS extension on my blog
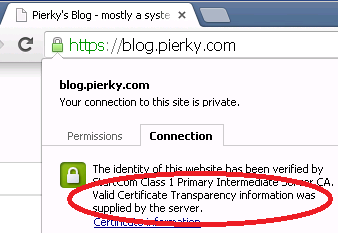
Finally, I managed to enable HTTPS on my own blog!
I opted for a quick-and-dirty solution based on a self-compiled version of HAProxy in front of WordPress, statically linked to OpenSSL 1.0.2, in order to serve Certificate Transparency information during the TLS setup.
RIPE Atlas Tracepath v0.3.0
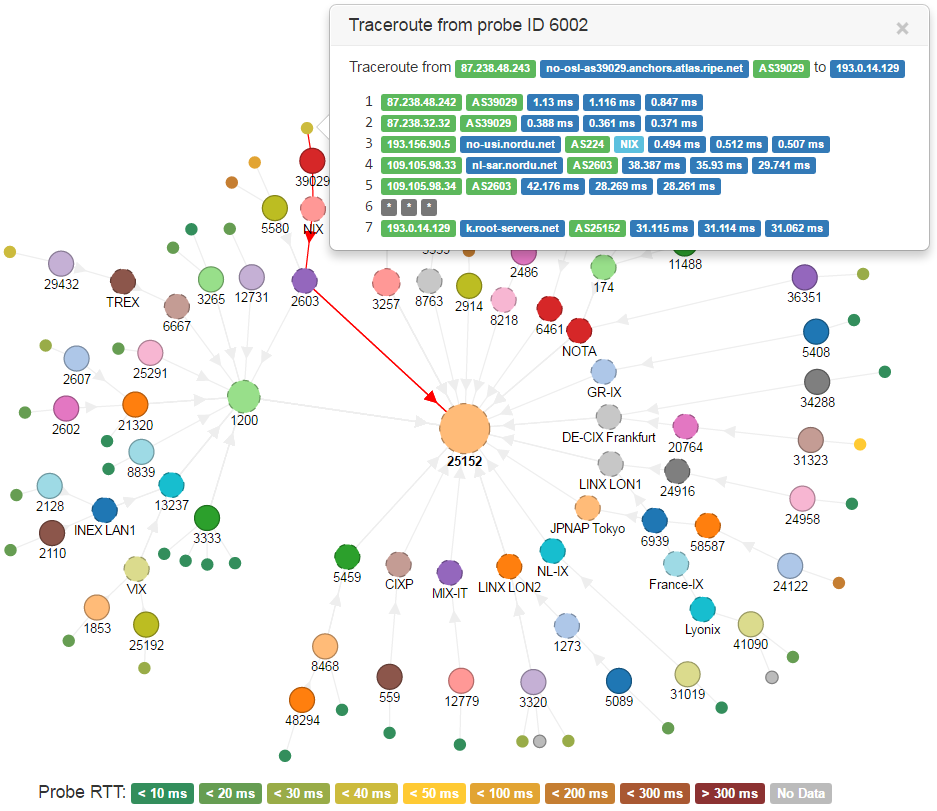
I released a new version of my web application RIPE Atlas Tracepath: v0.3.0. It reads results from RIPE Atlas traceroute measurements and shows Autonomous Systems that probes go through to reach the target.
UPDATE: new versions have been released since this post, with new features and bug fixes: please take a look at the project’s page on GitHub.
In the beginning it was a simple Python script/CGI; the new release has been totally rewritten, it’s now based on the D3.js visualization library and uses a more elegant Python backend based on Flask/WSGI.
Among the new features, probes are also displayed and linked to their origin AS; for those that completed the traceroute toward the target the avg RTT is also rendered in form of a scale of colors. Multiple Autonomous Systems can now be selected and moved together on the graph, in order to obtain the layout that best describes the analyzed scenario.
A demo can be found here. It only shows results from measurement ID 1674977, a traceroute from 50 probes all over the world toward www.ripe.net:
More details can be found on the GitHub page; feel free to use/edit/fork/improve it as you whish!
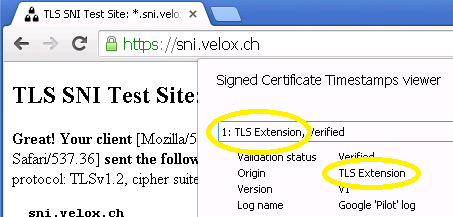
Certificate Transparency: manually verify SCT with openssl
The recent OpenSSL 1.0.2 version added support for Certificate Transparency (CT) RFC6962 by implementing one of the methods that allow TLS clients to receive and verify Signed Certificate Timestamp during the TLS handshake, that is the OCSP response extension. My goal here is to show how to use another method, the signed_certificate_timestamp TLS extension, to gain the same result.
SHA-1 sunset: valid SHA-2 chains treated as insecure
While dealing with the SHA-1 sunsetting process I encountered a problem with some certificates from StartSSL/StartCom that may lead Chrome to raise warnings or even errors on websites with updated SHA-2-only chains (at least on Microsoft Windows clients).