This is mostly a reminder to myself…
When you submit an openssl generated certificate signing request (CSR) file to a Windows Certification Authority and try to sign it you receive the following error:
The request contains no certificate template information. The request does not contain a certificate template extension or the CertificateTemplate request attribute.
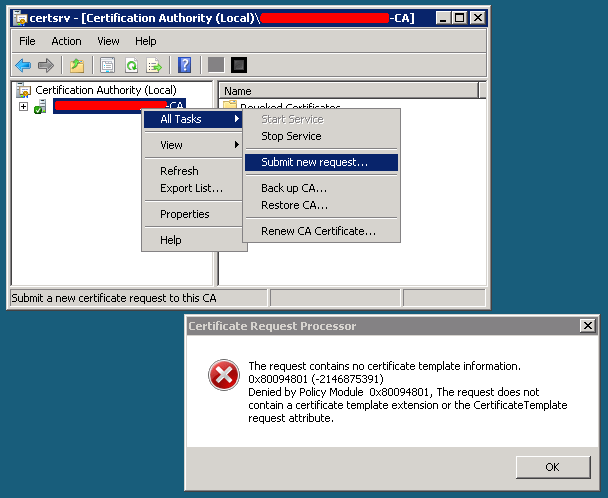
CA signing error – The request contains no certificate template information.
Every time (not really “every”!) I need to setup an Apache2 SSL certificate I get stuck in front of it!
Steps to have a domain-trusted SSL certificate installed on Apache2
1) Generate an SSL certificate signing request (CSR):
openssl req -new -newkey rsa:2048 -nodes -keyout server.key -out server.csr
2) Move the CSR file on the Windows server where the Certification Authority is running.
3) Open a DOS prompt with administrative privileges and run the following command:
certreq -submit -attrib "certificatetemplate:WebServer"
4) Now select the CSR file and then choose where to save the X.509 file.
You got it!
The WebServer name used in the certreq command is the name of the template you want to use, not the “display name”; you can have this parameter from the “Certificate Templates Console” MMC snap-in (certtmpl.msc):
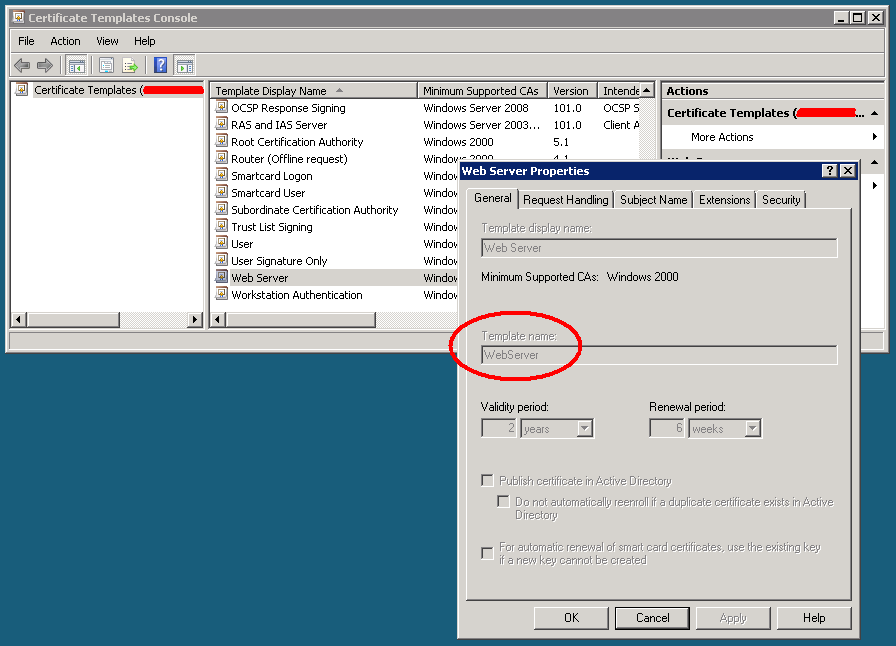
Template name from the Certificate Templates Console