These days I had to implement centralized terminal authentication on a few Cisco routers using aaa new-model and RADIUS.
The solution in its own was pretty simple: it was based on the usual Microsoft IAS (Internet Authentication Service) which was integrated in an Active Directory domain.
The interesting aspect is that those routers were under different administrative controls, so some users had to be granted access on a part of them and denied on other. Let’s say Group1 had to be enabled on routers RA, RB and RC, while Group2 on routers RD, RE and RF.
Solution adopted
In order to achieve this goal we may use a lot of solutions, but most of them are quite unscalable, because we have to map each router to the specific policy.
To obtain a good degree of scalability we may use the radius-server attribute 32 include-in-access-req command. This command tells IOS to append the NAS-Identifier attribute in the RADIUS authentication request message, and let us to set a format for its value:
RA(config)#radius-server attribute 32 include-in-access-req format ? LINE A string where %i = IP address and %h = hostname, %d = domain name
For example, we can prepend the router’s hostname with a “tag” to distinguish the owner group:
Group1 routers:
RA(config)#radius-server attribute 32 include-in-access-req format Group1-%h RB(config)#radius-server attribute 32 include-in-access-req format Group1-%h RC(config)#radius-server attribute 32 include-in-access-req format Group1-%h
Group2 routers:
RD(config)#radius-server attribute 32 include-in-access-req format Group2-%h RE(config)#radius-server attribute 32 include-in-access-req format Group2-%h RF(config)#radius-server attribute 32 include-in-access-req format Group2-%h
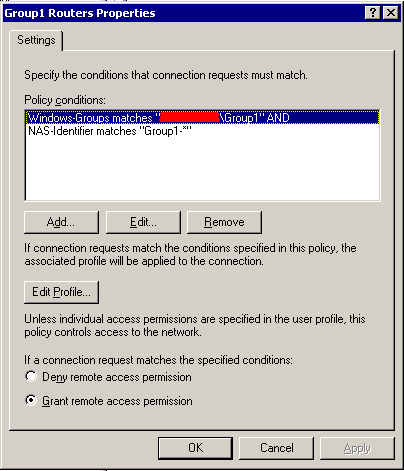 Finally we can create two policies in IAS to handle the incoming authentication requests, by filtering them on the basis of NAS-Identifier attribute.
Finally we can create two policies in IAS to handle the incoming authentication requests, by filtering them on the basis of NAS-Identifier attribute.
On the NAS-Identifier filter, we can use a star (“*”) to match any character which follows the router’s “tag”. Once we matched the router’s tag, we bind it to the right Active Directory group. Please take a look at the picture for details.
References
Cisco.com: Cisco IOS Security Command Reference, Release 12.3 T
Cisco.com: Command Lookup Tool
PacketLife.net Blog: Seven free ways to improve your network’s security
Kpjungle’s Weblog: Authentication by Radius on a Cisco device
Latest posts by Pier Carlo Chiodi (see all)
- Good MANRS for IXPs route servers made easier - 11 December 2020
- Route server feature-rich and automatic configuration - 13 February 2017
- Large BGP Communities playground - 15 September 2016
Leave a Reply