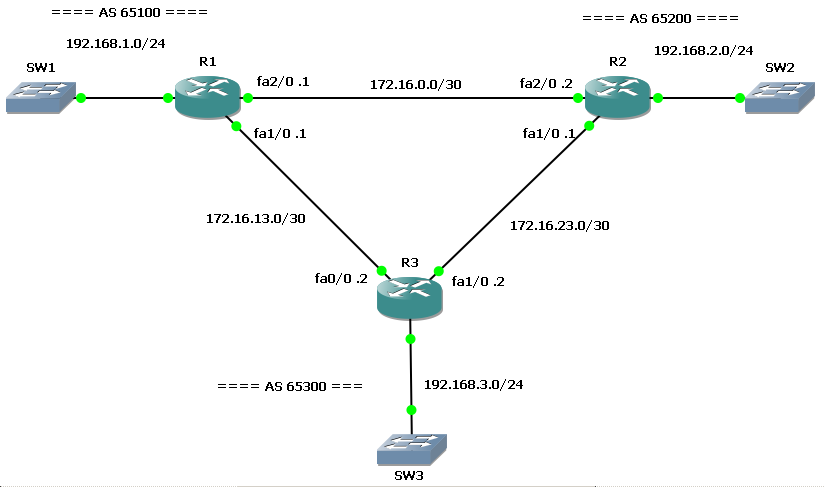
 The network … backdoor command let you to prefer IGP over eBGP routing updates without changing the overall BGP administrative distance.
The network … backdoor command let you to prefer IGP over eBGP routing updates without changing the overall BGP administrative distance.
Initially, R1 and R2 run an IGP (EIGRP) on the direct link (172.16.0.0/30).
R1#show ip route | beg Gateway
Gateway of last resort is not set
172.16.0.0/30 is subnetted, 2 subnets
C 172.16.13.0 is directly connected, FastEthernet1/0
C 172.16.0.0 is directly connected, FastEthernet2/0
C 192.168.1.0/24 is directly connected, FastEthernet0/0
D 192.168.2.0/24 [90/30720] via 172.16.0.2, 00:00:20, FastEthernet2/0
Look at D 192.168.2.0/24 [90/30720] via 172.16.0.2, 00:00:20, FastEthernet2/0.
Then, they start an eBGP peering session with R3…
R3#sh ip bgp
BGP table version is 10, local router ID is 192.168.3.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 192.168.1.0 172.16.13.1 0 0 65100 i
*> 192.168.2.0 172.16.23.1 0 0 65200 i
*> 192.168.3.0 0.0.0.0 0 32768 i
At this time, both R1 and R2 have an eBGP session with R3 and advertise their local networks: 192.168.1.0/24 and 192.168.2.0/24.
Now, looking at R1 (or R2) routing table, we can see they reach each other via R3:
R1#show ip route | beg Gateway
Gateway of last resort is not set
172.16.0.0/30 is subnetted, 2 subnets
C 172.16.13.0 is directly connected, FastEthernet1/0
C 172.16.0.0 is directly connected, FastEthernet2/0
C 192.168.1.0/24 is directly connected, FastEthernet0/0
B 192.168.2.0/24 [20/0] via 172.16.13.2, 00:02:16
B 192.168.3.0/24 [20/0] via 172.16.13.2, 00:02:16
Look at B 192.168.2.0/24 [20/0] via 172.16.13.2, 00:02:16
Why? What appened? This is not an optimal routing plan!
With BGP peering on, R3 receives R1 (and R2) networks, then it advertise them back to the other peer: the eBGP administrative distance is lower than IGP (EIGRP and others), so R2 (and R1) prefer the route through R3.
To avoid this behaviour you can change BGP administrative distance with distance bgp command, but this is not recommended… or you can use the network backdoor command.
You can apply this command on one peer to tell it to prefer IGP for a given network:
R1(config)#router bgp 65100
R1(config-router)#network 192.168.2.0 mask 255.255.255.0 backdoor
R2(config)#router bgp 65200
R2(config-router)#network 192.168.1.0 mask 255.255.255.0 backdoor
Now back to the routing tables:
R1#show ip route | beg Gateway
Gateway of last resort is not set
172.16.0.0/30 is subnetted, 2 subnets
C 172.16.13.0 is directly connected, FastEthernet1/0
C 172.16.0.0 is directly connected, FastEthernet2/0
C 192.168.1.0/24 is directly connected, FastEthernet0/0
D 192.168.2.0/24 [90/30720] via 172.16.0.2, 00:00:30, FastEthernet2/0
B 192.168.3.0/24 [20/0] via 172.16.13.2, 00:10:29
The route is again reached via the local link!
If the R1-R2 link goes down…
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#int fa2/0
R2(config-if)#shu
R2(config-if)#shutdown
R2(config-if)#
*Mar 1 00:21:13.195: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 65100: Neighbor 172.16.0.1 (FastEthernet2/0) is down: interface down
*Mar 1 00:21:15.059: %LINK-5-CHANGED: Interface FastEthernet2/0, changed state to administratively down
*Mar 1 00:21:16.059: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet2/0, changed state to down
… the R2’s network is still reachable via R3:
R1#show ip route | beg Gateway
Gateway of last resort is not set
172.16.0.0/30 is subnetted, 2 subnets
C 172.16.13.0 is directly connected, FastEthernet1/0
C 172.16.0.0 is directly connected, FastEthernet2/0
C 192.168.1.0/24 is directly connected, FastEthernet0/0
B 192.168.2.0/24 [200/0] via 172.16.13.2, 00:00:17
B 192.168.3.0/24 [20/0] via 172.16.13.2, 00:11:43
You can find on the .zip file 3 config versions (config subdir): “1. Interfaces and IP”, “2. EIGRP + BGP” and the final configuration with the network … backdoor command.
Download the lab here!