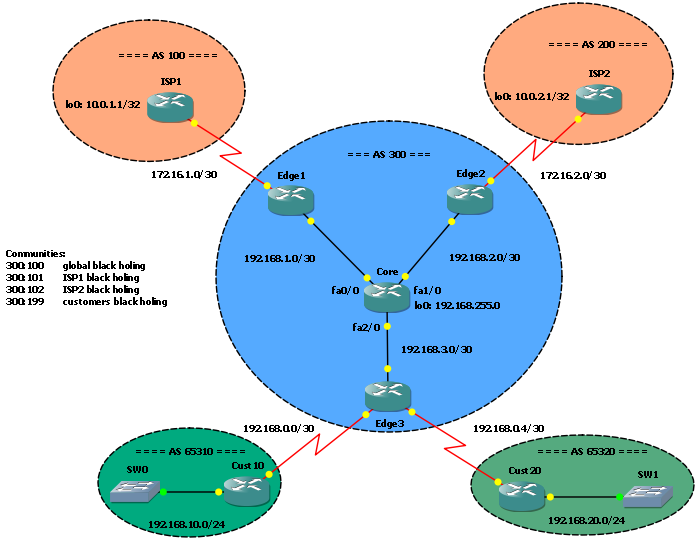
You can monitor Radius (and other services too, such as DNS and other) with Zabbix external check feature and netcat (nc).
How do external check items work?
“External check” items are monitored by Zabbix using external scripts, running on the server; you can create your own scripts and put them in the ExternalScripts directory, as defined by the zabbix_server.conf file:
# Location of external scripts
ExternalScripts=/etc/zabbix/externalscripts
You can setup an external check item using the following syntax for the key parameter:
Type: External check
Key: script[parameters]
For example, you can configure Zabbix to run the script checkradius.sh and to pass it the host IP address:
Description: Radius – Authentication
Type: External check
Key: checkradius.sh[{IPADDRESS}]
Type of information: Numeric (unsigned)
Zabbix will execute checkradius.sh HOSTNAME|HOSTIPADDRESS IPADDRESS, where HOSTNAME|HOSTIPADDRESS is the host name or IP address (it depends on the “Connect to” host parameter), and IPADDRESS is the value of the macro {IPADDRESS} used as parameter.
How to use netcat with external check items
With netcat (nc) you can send a host UDP or TCP data and get a response from it. For example, you can send a Radius authentication packet and wait for a response from the server.
Of course Netcat knows nothing about Radius or other protocols, it simply sends and receives data, so you have to forge an Access-Request packet and to parse an Access-Accept response.
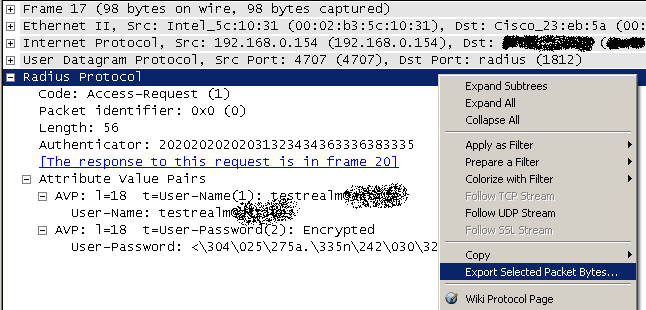 To build the Radius Access-Request packet I simply sniffed a real packet using Wireshark and then I exported it to my Zabbix server (you can see it in the picture).
To build the Radius Access-Request packet I simply sniffed a real packet using Wireshark and then I exported it to my Zabbix server (you can see it in the picture).
Once you have sent the Access-Request packet, you should receive an Access-Accept response from your server, so you can parse the response to see if it is the one you expected. You can do this using od to convert netcat output in hex and then grep the Radius Access-Accept code (0x02).
External check item and script configuration
My script uses only one argument, the one Zabbix always passes to external scripts, so I did’nt configure it to pass other parameters:
Description: Radius – Authentication
Type: External check
Key: checkradius.sh[]
Type of information: Numeric (unsigned)
The script gets the Radius packet to send to the server from the $1.rad file, where $1 is the host name or IP address; for example, for the Radius server at 10.0.0.1 I will put the Access-Request packet in the 10.0.0.1.rad file.
EDIT 2011-10-13: I think I forgot the “#! /bin/bash” line!
UPDATE 2011-12-01: I added the timelimit command to the script (you can install it with apt-get install timelimit). This command runs another command (nc in my script) and kills it after a specified time lapse. This is useful to handle endless netcat timeout. Remember to raise the default Timeout in the Zabbix configuration file in order to match your command timeout (file /etc/zabbix/zabbix_server.conf, parameter Timeout=10).
#! /bin/bash
cat /etc/zabbix/externalscripts/$1.rad |
timelimit -q -t 5 -T 5 nc -u -w 1 $1 1812 | od -t x1 |
grep "0000000 02" > /dev/null
if [ $? == 0 ]; then
echo 1
exit 1
else
echo 0
exit 0
fi
References
Radius RFC: http://www.ietf.org/rfc/rfc2865.txt
Zabbix: http://www.zabbix.com/
Netcat: http://netcat.sourceforge.net/
Wireshark: http://www.wireshark.org/