 AToM stands for Any Transport over MPLS, a quite reassuring technology which, provided you have a MPLS enabled network and some good gears, let you set up L2 circuits across your IP backbone.
AToM stands for Any Transport over MPLS, a quite reassuring technology which, provided you have a MPLS enabled network and some good gears, let you set up L2 circuits across your IP backbone.
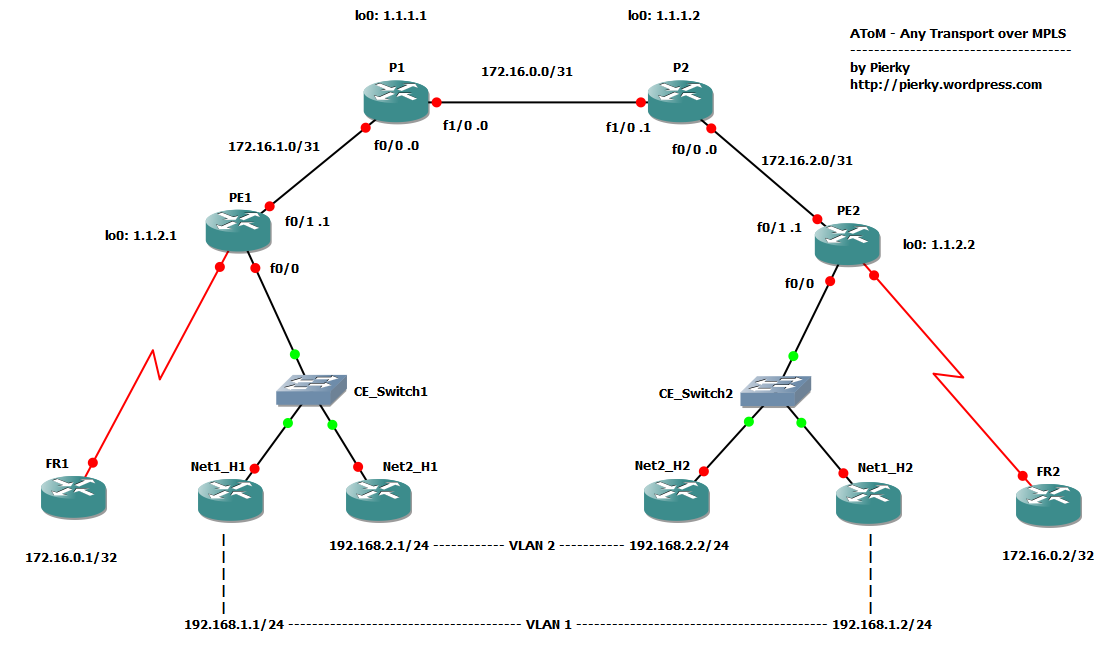
This lab offers a very simple topology with 2 AToM links; an ethernet with an 802.1q trunk and a frame-relay link.
Core
Core (P) routers configuration is pretty simple; we only enable MPLS switching on interfaces toward PE routers and setup LDP for labels exchange. A good core doesn’t care about what kind of traffic it switches!
P1:
mpls label protocol ldp
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface FastEthernet0/0
description PE1 facing interface
mpls ip
!
interface FastEthernet1/0
description P2 facing interface
mpls ip
!
mpls ldp router-id Loopback0 force
PE routers
The hard work is done on PE routers. PE routers face CE routers, which they receive L2 traffic from, and network core P routers, which they have to send MPLS encapsulated traffic to.
In order to build up a L2 circuit, PE routers have to setup a pseudowire connection between them, so they know how to switch traffic. Each pseudowire uses a virtual-circuit ID (VC ID), which is locally significant on each PE pair and is used to identify the pseudowire itself and to bind it to a specific MPLS label.
First off, they must be MPLS aware:
PE2
mpls label protocol ldp
!
interface Loopback0
ip address 1.1.2.2 255.255.255.255
!
interface FastEthernet0/1
description P2 facing interface
mpls ip
!
mpls ldp router-id Loopback0
Now, we have to set up pseudowires between PE and L2 connections with CEs.
Let’s start with the Ethernet 802.1q trunk.
Port mode Ethernet over MPLS (EoMPLS)
In port mode EoMPLS every frame received on a PE interface is forwarded to the other PE almost unchanged (just preamble and FCS are removed).
Basic configuration is very simple:
PE2
interface FastEthernet0/0
description CE_Switch2 facing interface
no ip address
duplex auto
speed auto
xconnect 1.1.2.1 10 encapsulation mpls
The xconnect command does all the work! This command tells the PE router to encapsulate every frame in a MPLS packet and to forward it to the peer 1.1.2.1 using VC ID 10.
It also allow Label Distribution Protocol (LDP) to exchange informations about the pseudowire circuit between PEs (VC ID / label mapping, VC type, MTU).
Once we have applied this configuration to both PE routers (on PE1 we have to change the xconnect peer address!), we can verify if LDP did its work and if pseudowire is up:
PE2#show mpls l2transport vc 10 detail
Local interface: Fa0/0 up, line protocol up, Ethernet up
Destination address: 1.1.2.1, VC ID: 10, VC status: up
Output interface: Fa0/1, imposed label stack {18 16}
Preferred path: not configured
Default path: active
Next hop: 172.16.2.0
Create time: 01:16:07, last status change time: 01:15:44
Signaling protocol: LDP, peer 1.1.2.1:0 up
MPLS VC labels: local 16, remote 16
Group ID: local 0, remote 0
MTU: local 1500, remote 1500
Remote interface description:
Sequencing: receive disabled, send disabled
VC statistics:
[cut]
Now, setup and test VLAN connectivity on customer side:
Net1_H1#sh run int fa0/0 | beg interface
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
duplex auto
speed auto
end
Net1_H2#sh run int fa0/0 | beg interface
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
duplex auto
speed auto
end
Net1_H1#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 148/168/192 ms
Frame-relay over MPLS, DLCI-to-DLCI mode
Frame-relay over MPLS requires a few more lines of configuration, but the pseudowire setup is the same as EoMPLS.
We have to enable frame-relay switching on the PE router, configure the Serial interface as DCE and setup the switching path for the DLCI:
PE2
frame-relay switching
!
interface Serial1/0
no ip address
encapsulation frame-relay IETF
frame-relay intf-type dce
!
connect FR2-FR1 Serial1/0 201 l2transport
xconnect 1.1.2.1 20 encapsulation mpls
PE1
frame-relay switching
!
interface Serial1/0
no ip address
encapsulation frame-relay IETF
frame-relay intf-type dce
!
connect FR1-FR2 Serial1/0 102 l2transport
xconnect 1.1.2.2 20 encapsulation mpls
Let’s verify everything is ok:
PE2#show mpls l2transport vc 20
Local intf Local circuit Dest address VC ID Status
------------- -------------------------- --------------- ---------- ----------
Se1/0 FR DLCI 201 1.1.2.1 20 UP
With this configuration we have DLCI 102 for FR1-to-FR2 traffic, and DLCI 201 for FR2-to-FR1 traffic.
Customer side configuration:
FR1
interface Serial0/0
no ip address
encapsulation frame-relay IETF
!
interface Serial0/0.1 point-to-point
ip address 172.16.0.1 255.255.255.252
frame-relay interface-dlci 102
Similar configuration on FR2:
interface Serial0/0.1 point-to-point
ip address 172.16.0.2 255.255.255.252
frame-relay interface-dlci 201
Some tests…
FR1#show frame-relay lmi
LMI Statistics for interface Serial0/0 (Frame Relay DTE) LMI TYPE = CISCO
Invalid Unnumbered info 0 Invalid Prot Disc 0
Invalid dummy Call Ref 0 Invalid Msg Type 0
Invalid Status Message 0 Invalid Lock Shift 0
Invalid Information ID 0 Invalid Report IE Len 0
Invalid Report Request 0 Invalid Keep IE Len 0
Num Status Enq. Sent 615 Num Status msgs Rcvd 573
Num Update Status Rcvd 0 Num Status Timeouts 42
Last Full Status Req 00:00:24 Last Full Status Rcvd 00:00:24
FR1#
FR1#show frame-relay pvc
PVC Statistics for interface Serial0/0 (Frame Relay DTE)
Active Inactive Deleted Static
Local 1 0 0 0
Switched 0 0 0 0
Unused 0 0 0 0
DLCI = 102, DLCI USAGE = LOCAL, PVC STATUS = ACTIVE, INTERFACE = Serial0/0.1
input pkts 115 output pkts 120 in bytes 32266
out bytes 33844 dropped pkts 0 in pkts dropped 0
out pkts dropped 0 out bytes dropped 0
in FECN pkts 0 in BECN pkts 0 out FECN pkts 0
out BECN pkts 0 in DE pkts 0 out DE pkts 0
out bcast pkts 100 out bcast bytes 31764
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
pvc create time 01:43:39, last time pvc status changed 01:10:26
FR1#
FR1#ping 172.16.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 164/185/220 ms
Please note how the subnet 172.16.0.0/32 on the FR routers does not conflict with 172.16.0.0/31 between P routers; it’s on a totally different L3 domain and it is not routed by the network, but transparently encapsulated in L2 over MPLS packets.
Packet captures
You can find some nice packet captures about this lab at PacketLife.net Captures section, under the MPLS category; they have been taken on P1-P2 link, with inner (pseudowire) and outer MPLS label on top of every packet. They are “LDP_Ethernet_FrameRelay”, which shows how LDP setup the pseudowire circuit, “EoMPLS_802.1q” and “Frame-Relay over MPLS”, which show an ICMP ping encapsulated in Ethernet and Frame-relay respectively.
Anyway, if you don’t know PacketLike.net you must take a tour of that great website, really worth it!
Conclusion and download
This post only shows a little basic configuration of some AToM solutions; there are many more capabilities than which I wrote on this blog. A good starting point is to read documents you can find using links below.
If you want to download this GNS3/Dynamips lab, you can find it here.
References
Cisco.com: MPLS AToM Technical Overview
Cisco.com: Any Transport over MPLS