You know when in the morning you wake up and a thought flashes across your mind? One of these mornings I had this: how many RIPE Atlas probes are on a NAT64/DNS64 scenario? RFC7050 can help to answer this question.
DNSSEC: ECDSA-aware resolvers seen by RIPE Atlas
A couple of days ago CloudFlare announced its public alpha release of their DNSSEC implementation. Since they are using the “recent” Elliptic Curve ECDSA P-256 (RFC6605) I wondered how many resolvers can have problems with signatures validation so I wanted to take a peek at the current situation as seen by the RIPE Atlas probes network.
Verifying DKIM signatures on Thunderbird with DNSSEC
I’m happy to see that more and more tools are developed to increase the security level and trustworthiness of Internet applications. I already talked about DNSSEC and tools to check the validity of domain names, many others blogged about DANE and TLSA validation support in browsers; this time I would like to focus on DKIM and on a Thunderbird add-on to verify its signatures taking advantage of DNSSEC end-to-end validation.
DNSSEC-aware resolvers among RIPE Atlas probes
After reading the interesting post by Stéphane Bortzmeyer on RIPE Labs (How Many RIPE Atlas Probes Can Resolve IPv6-only Domain Names?) I wondered how many RIPE Atlas probes used DNSSEC aware resolvers, so I tried to setup some measures and some comparisons.
As also expressed in the aforementioned post, it should be noted that RIPE Atlas probes can’t be used to represent general behaviors of Internet users; they are excellent “toys” in the hands of network engineers but nobody can ensure that their configuration reflects the one used in production environments by users or by servers or by applications.
DNSSEC secured blog: raising awareness on DNS security
Hurray! My blog and the whole pierky.com domain are now running on a DNSSEC secured zone.
Thanks to the recent moving of the blog from the WordPress.org hosted infrastructure to the OVH hosting service I finally managed to enable IPv6 and DNSSEC support.
If you are using a DNSSEC-aware resolver (are you? check it out…) you can verify it yourself:
:~# dig +dnssec blog.pierky.com ; <<>> DiG 9.8.1-P1 <<>> +multi +dnssec blog.pierky.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31643 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ...
There it is the ad (Authenticated answer) flag.
If your resolvers are not DNSSEC-aware – what a shame! Tell your ISP to enable them 🙂 – you can try the same using an open resolver which supports DNSSEC, like those of Google…
:~# dig +dnssec blog.pierky.com @8.8.8.8
… or you can try an online test suite, like the one provided by Verisign Labs or DNSViz.
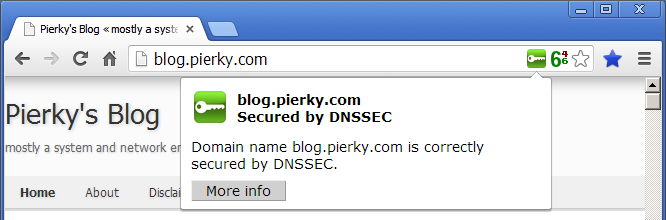
A nice browser addon – available for Internet Explorer, Firefox and Chrome – allows you to check the DNSSEC validity of the domain names in your browser window. It’s name is DNSSEC Validator and it works even if your resolvers are not DNSSEC enabled (you can set an external resolver different from the one in use in your operating system); here it is a screenshot showing my blog’s status:
(in the above screenshot you can see a green 6 too, originated from another Chrome addon, IPvFoo, which indicates whether the current page was fetched using IPv4 or IPv6).
This is just a small drop in the ocean of Internet, but I like to believe that it might raise awareness about DNS security matter and encourage its adoption (it seems that as of September 2012 only 1.7% of the visible DNS resolvers in the Internet were performing DNSSEC validation).
References
RIPE Labs – Counting and Re-Counting DNSSEC
dnssec-deployment.org – DNSSEC in ccTLDs, Past, Present, and Future/
dnssec-deployment.org – ccTLD DNSSEC Adoption as of 2013-07-30 [PDF]
CZ.NIC – DNSSEC Validator
Verisign Labs – Test if you are benefiting from DNSSEC
Verisign Labs – DNSSEC-Debugger
Sandia.gov – DNSViz