I’m 3 hours from the beginning of my trip to Scotland, but I don’t want to leave unanswered a question that Moh asked me on my previous Dual WAN connection on Cisco with Policy-based routing (PBR) post.
Scenario and Objectives
Scenario and objectives are kindly provided by Moh!
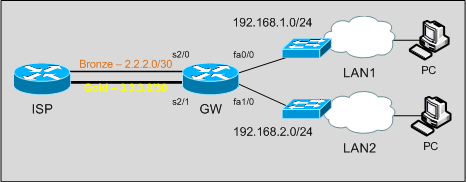
I have a situation same like this, I will give an brief idea. this is for one of my client, they have two leased line connection and using 2801 router it connected to two lan networks(say for 192.168.1.0, 192…2.0/24) they just wanna divide the complete traffic based on internal network. one of the internal(1.0/24) network traffic should go through wan1 (complete traffic, no matter what it is) and other one has (2.0/24) to go through wan2
Solution
The solution, as in the previous post, is based on PBR (Policy Based Routing). It’s a quite simple use of PBR in this case; as Moh says:
It is very easy to do in fortinet and juniper. but i’m bit confused in cisco now.
Of course, it’s easy using Cisco & IOS too! 😉
I post it here with the hope it could be helpful to someone – other Moh, of course! 🙂
As first, routing policies: what traffic we want to route where?
LAN1 traffic through the Bronze link, LAN2 traffic through the Gold link. We want LAN-to-LAN reachability too.
We define an access list which matches all traffic towards subnets out of our network:
access-list 199 deny ip any 192.168.0.0 0.0.255.255 access-list 199 permit ip any any
If we don’t exlude 192.168.0.0/16 our route-maps policies will also be applied to LAN-to-LAN traffic.
Then we make route-maps and apply them to LAN interfaces:
route-map LAN1 permit 10 match ip address 199 set interface Serial2/0 route-map LAN2 permit 10 match ip address 199 set interface Serial2/1 interface FastEthernet0/0 description LAN1 ip address 192.168.1.1 255.255.255.0 ip nat inside ip policy route-map LAN1 interface FastEthernet1/0 description LAN2 ip address 192.168.2.1 255.255.255.0 ip nat inside ip policy route-map LAN2
Now, routing is Ok; traffic coming from LAN1 with destinations different from LAN2 subnet will be routed out S2/0. Same for LAN2 traffic, out S2/1.
Now, we have to build policy-based NAT: traffic out the S2/0 interface has to be translated using S2/0 IP address; same for traffic coming out from S2/1, translated with S2/1 address.
route-map NAT_LAN1 permit 10 match interface Serial2/0 route-map NAT_LAN2 permit 10 match interface Serial2/1 ip nat inside source route-map NAT_LAN1 interface Serial2/0 overload ip nat inside source route-map NAT_LAN2 interface Serial2/1 overload
Tests
Pings from the LAN (in the GNS3-Lab PCs are routers) to “internet” (4.4.4.4) are routed accordingly to what expected:
GW#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 2.2.2.2:6 192.168.1.10:6 4.4.4.4:6 4.4.4.4:6 icmp 3.3.3.2:6 192.168.2.10:6 4.4.4.4:6 4.4.4.4:6
If you want to try this in GNS3 please download the lab from the previous post; just few changes are required!
Disclaimer
This post has been written while 85% of my little brain is thinking about Nessie, castle ghosts and left-hand car driving; I hope I didn’t write nonsense!
Latest posts by Pier Carlo Chiodi (see all)
- Good MANRS for IXPs route servers made easier - 11 December 2020
- Route server feature-rich and automatic configuration - 13 February 2017
- Large BGP Communities playground - 15 September 2016
Great info.. Really thanks for considered my scenario.
Really thanks again!!!
I will disturb you always with more doubts;) bcoz simply I like you:)
Thanks, you are welcome! 😉
It’s Nessie time now! 🙂
Bye
Really sorry, could you please clarify this area?
access-list 199 deny ip any 192.168.0.0 0.0.255.255
access-list 199 permit ip any any
If we don’t exlude 192.168.0.0/16 our route-maps policies will also be applied to LAN-to-LAN traffic.
PBR applies to all the traffic coming into the interfaces from LAN1 and LAN2 that matches the route-map match statements.
Suppose you don’t exclude local subnets from the route-map scope: a packet from 192.168.1.0/24 to 192.168.2.0/24 would be matched by the route-map and routed to the s2/0 interface; but we don’t want this behaviour, we want that packet to be routed to the other LAN interface. If you deny those packets the route-map does not match them, so they are routed using the standard routing table.
ok, Brilliant…
So in that way even we don’t want to use any iproute to the gateways? just for a note, in a real environment the internal network comes like vlan based, which means there should be a core switch and which have vlans and those vlans are routed in the core switch itself…
Also just wana ask if you dont mind, what will happen incase if there is a third network or if there is any guest network added? just need to create another policy with deny and add to interface, right?
You can add interfaces (even dot1q tagged) and PBR policies, or you can achieve same isolation with more scalability using VRF. If you have a lot of isolated internal networks I think it should be the case to consider VRF.
OK,Great. I guess we don’t want to use VRF in this case, its not that much complex network.anyway I will get back you soon once i there on the site, then only i can give a clear picture… I believe that you can help me out this.. :)I just +4 GMT far away from you(UAE, Dubai)
Well, Really thanks again for your valuable time spending for me!
Take care!
Hi there,
I would like to clear few things again with you, as i said our project implementation almost completed. they have two procurve core switches and which have more than 20vlans, it working based on load balancinb(divided the vlans on instance based, so half of the vlan will take an link to reach the core1 switch, rest of the vlans will go through the core2 switch) plus HSRP,routing is enabled on the core switch , in that way all the vlans can communicate. around 150 procurve switches are connected to the core switch with full redundancy in lan area.
Now from here we are going to start the cisco work,
they have two ethernet leased line connection, which we want to connect to the 2800 series router. The actual requirement is they need 10 of the vlans should go through the first leased line and all other should go through the second leased line interface.do we need to go for VRF? or can we use PBR?
just note that in addition, there will be a ASA 5520 will come on this network.
please let me know incase if you need more information regarding this.
Really thanks again for your quick replies.
the same like as above diagram, but will increase the number of lan network and working vlan based, the core switch admin network will connect to the router(say for the admin IPs are the same like above) We just bit confused about the cisco configuration for this..
Hi Moh, as far as I understand Vlans are not isolated, they can communicate between them; I think PBR is fine.
Bye
ok, great…so i can go with the above method, right?
do i need to care anything special on this scenario?
I think you can go, I don’t see possible issues… of course, only you can have the full feeling of this scenario!
ok, thanks…
i will let you know incase if i face something wrong…:)
really thanks
Hi,
I have a situation with 2WANS and one LAN.
NAT is required to go out from the LAN to the WAN links.
I need to send certain traffic (within an access-list A) to WAN1 and other type of traffic (within access-list B) to WAN 2.
How can this be done?
Thanks,
Hi,
you can solve it using what I wrote in the post. Just consider one LAN!
Let all the traffic to go out using WAN2 (default route) and intercept “interesting traffic” with a route-map and PBR: match access-list A / set interface WAN1.
Bye
Hey Thanks.
Very helpful indeed. I managed to get it to work.
Cheers!
excelente !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Slds desde Chile
Say for example you wanted to setup two different WAN (dsl) connections, one for voice traffic and one for data. Would the following commands work?
CCME – 192.168.1.5
ATM0/0/0
description DSL for Data
ip policy route-map DATA
ATM0/0/1
description DSL for Voice
ip policy reoute-map VOICE
route-map DATA permit 10
match ip address 1
set interface ATM0/0/0
route-map VOICE permit 20
match ip address 2
set interface ATM0/0/1
accesslist 1 “DSL for Data ONLY”
deny 192.168.1.5 any any
allow any any
accesslist 2 “DSL for VoIP ONLY”
allow 192.168.1.5 any any
deny any any
Please take a look at this post: http://blog.pierky.com/2009/03/28/dual-wan-connection-on-cisco-with-policy-based-routing-pbr/
PBR route-map should be applied to LAN interface, not WAN.