I’m happy to see that more and more tools are developed to increase the security level and trustworthiness of Internet applications. I already talked about DNSSEC and tools to check the validity of domain names, many others blogged about DANE and TLSA validation support in browsers; this time I would like to focus on DKIM and on a Thunderbird add-on to verify its signatures taking advantage of DNSSEC end-to-end validation.
DKIM
DKIM is a mechanism to build and verify a trust relationship between an email message and a domain name (usually the sender’s one). When an email message is sent, the sending mail server cryptographically signs its contents using the private part of an asymmetric key and adds a reference back to the public part of the key, that is published under the DNS zone of the sending domain.
Since message recipients base the validation on public keys published via DNS records, it’s important to be sure that data obtained through DNS queries is valid; here DNSSEC takes to the field.
Validation may occur both in the email server which holds the recipient’s mailbox or in the email client running on a user’s device: in the first case a local policy (or a DMARC policy, but this is off-topic for this post) defines what to do with the message (drop it, mark it as spam, …); in the second case the user’s client can show a warning if signature validation fails or a confirmation message if everything is fine. Here I’ll cover the second case.
Thunderbird DKIM Verifier add-on
I came across DKIM Verifier, an interesting add-on for Mozilla Thunderbird that checks DKIM signatures on the client-side and which supports a DNSSEC backend to ensure end-to-end DNS security. I tested the Windows version with good results.
The add-on can be configured to fetch DKIM DNS keys using two methods: a JavaScript DNS library, limited to simple TCP queries, or libunbound, a validating recursive DNSSEC library. To use the second method, the only one that gurantees end-to-end DNSSEC validation of DKIM keys, another add-on must be installed: DNSSEC Validator. At time of writing, only the 2.0.1 version includes libunbound, while the official one (1.1.5) does not.
Installation
Installation is built on two-steps: installing DNSSEC Validator (required to use libunbound) and then installing DKIM Verifier. Do it at your own risk.
After downloading the DNSSEC Validator 2.0.1 version, I installed it following the “Installing add-ons downloaded from outside Thunderbird” guide. As stated in the DKIM Verifier DNS Wiki page “the DNSSEC Validator add-on must only be installed, not enabled for this to work”, so I disabled it from the Thunderbird Tools / Add-ons interface.
Then I installed the DKIM Verifier from within Thunderbird, via the Tools / Add-ons interface.
Configuration
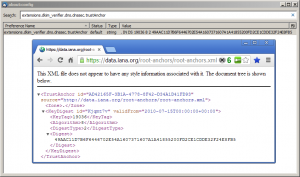
Since security and reliability of this solution rely on DNSSEC, we should verify that the trust anchor used by libunbound corresponds to the one used in the root zone: from the Thunderbird Config Editor search for the extensions.dkim_verifier.dns.dnssec.trustAnchor parameter and check that its value matches the one published at the root zone.
Then, from the Thunderbird Tools / Add-ons interface, open the DKIM Verifier options window and, in the DNS tab, select the libunbound option from the Resolver list. “Then set the path to libunbound to extensions/dnssec@nic.cz/plugins/ub_ds_windows-x86.dll and enable Path relative to profile directory” (more details on the DKIM Verifier DNS Wiki page). Many other settings are available in the options window, take a look at them to fully customise your configuration.
Finally, restart Thunderbird to ensure that new settings will be loaded.
Testing
Now, when you open a message that is signed using a DKIM header, Thunderbird will verify its signature and will show the results:
The add-on detects that the message is signed with a DKIM header, parses it and extracts the signing domain (d=nic.cz) and the selector (s=default):
DKIM-Signature: v=1; a=rsa-sha256; c=simple/simple; d=nic.cz; s=default;
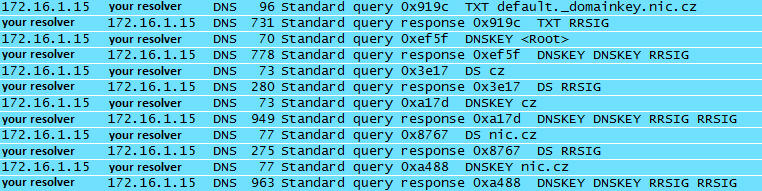
Then, it uses libunbound to acquire the public DKIM key via DNS, sending a query of type TXT to selector._domainkey.domain (you can do it manually with dig default._domainkey.nic.cz TXT on a Linux shell or nslookup -querytype=TXT default._domainkey.nic.cz on Windows prompt).
This is what happens behind the scenes, as seen from Wireshark…
… and from the Thunderbird error console (Tools / Error console):
The libunbound library takes care of DNS data lookup and possible DNSSEC end-to-end validation, from the root zone down to the domain level.
Of course, in order to have the “secure: true” output you must not only receive a message that is signed with DKIM headers, but it must be under a DNSSEC-secured domain also. In the example I used a message from the CZ domain registry, whose domain (nic.cz) is protected by DNSSEC. For example GMail, at time of writing, signs outgoing messages with DKIM but its domain is not protected by DNSSEC. The DKIM Verifier Options window, in the Advanced tab, offers some options on how to treat keys which are not signed by DNSSEC.
Please note that libunbound uses cache mechanisms to reduce network traffic: validations following the first one may not require DNS queries toward root zone or TLD if DNSSEC information have already been received.
More…
– DKIM official home-page: http://www.dkim.org/
– DKIM on WikiPedia: http://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
– DKIM Verifier Thunderbird add-on on GitHub: https://github.com/lieser/dkim_verifier
– Unbound: http://www.unbound.net/
Latest posts by Pier Carlo Chiodi (see all)
- Good MANRS for IXPs route servers made easier - 11 December 2020
- Route server feature-rich and automatic configuration - 13 February 2017
- Large BGP Communities playground - 15 September 2016


If running linux you can skip most of the above. Just install https://addons.mozilla.org/en-US/thunderbird/addon/dkim-verifier/
Then under addons -> dkim verifier -> preferences -> DNS -> uncheck under profile -> select /usr/lib/…/libunbound….
That’s it, works great.